Industrial Espionage
Strategic Implications
in an Age of Crime and Competition
I. Introduction
Industrial espionage of all varieties, whether merely competitive intelligence, semi-legitimate technology transfer or outright theft, is an elusive and secretive field, one deserving of careful attention not only by government agencies but by industrial managers and corporate executives both in the United States and abroad. This report will focus on several key aspects of industrial espionage as they pertain to contemporary American industry. It is anticipated that elucidation of primary data, some of which is quite alarming, will draw attention to the strategic risks and dangers inherent in ignoring on-going, already excessively wide-spread espionage activities conducted both from within this nation's vital industries and from external bases of operation.
The ultimate 'stakes' are quite high and are related literally to national survival since they affect military strength and industrial dominance. The thrust of hostile intelligence operations can endanger U.S. interests whether these operations come from abroad, are conducted abroad or are centered closer to home in the very towns and suburban neighborhoods where technological and state-of-the-art devices are developed, tested and perfected. There are both "open and covert" approaches, either of which can be extremely costly to U.S. industrial interests, depending on the magnitude, scope and intent of the incursion. These operations are conducted on an on-going basis, although some types may be more intense at particular times. There may be a "lag effect"of, for example, several months after an international crisis when foreign governments take stock of their strategic posture and decide that they need to strengthen certain sectors of their economy or military preparedness. After the change in governments in Iran, as a case in point, several months elapsed before Iranian intelligence operations reached their peak in countries perceived as hostile to Iran's interests. The inter-relatedness of the political motive and the economic motive is frequently a characteristic of industrial espionage, as in the case of Iran, and sometimes delays occur between a triggering incident and a campaign of infiltration and industrial intelligence-gathering. In a general sense, there is a tremendous temptation to engage in such illicit behavior (its degree of legality varies, as will be discussed) and even perfectly legitimate business executives, engineers or specialists fall victim to what they perceive as a relatively easy task, i.e. the purloining of either raw information or refined technical processes.
Efforts to curtail industrial espionage are referred to, just as in the world of political intrigue, as counter-intelligence operations. Major corporations, often with the support of government agencies, spend vast sums of money to protect against infiltration of their data bases, their industrial or manufacturing facilities or their technical or chemical laboratories. Frequently entire departments are established within large corporations to brainstorm and strategize as necessary. Specialists and consultants are called in to effectively counter actual or potential assaults on trademarked products, computer-stored data or high-level technological developments. In extreme cases of espionage, as will be discussed, official investigations are launched and prosecution or international "pursuit" results.
Methods for detecting and dealing with industrial intelligence operations range from simple internal verification procedures to involvement of major federal agencies such as the FBI, MI-6 or the SDECE, in the cases of the United States, the United Kingdom and France respectively. They investigate false identities, newspaper credentials, student visas and other possible covers, often detecting irregularities which the industries themselves fail to notice.
This report will delve into all of these practices, and will attempt to assess the extent, nature and degree of the current threat to the United States, with occasional reference to both England and France, all major industrial powers, sometimes acting collaboratively and at other times very much at odds in the tough competitive world of domestic and international business. Mentioned, briefly in passing, will also be the role of banking, of raw materials-industries, of import-export patterns, technology transfer initiatives, and other vulnerable sectors, notably the most recent developments in computer software and in armaments. It is astonishing that, in all, more than 100 billion dollars annually in sales losses are drained out of the U.S. economy due to industrial intelligence operations and corporate espionage (CRIIR, July 1997, 3). Other sources place these U.S. losses as high as 250 billion dollars per year (CNN-FN, Mar 9, 1999).
As can be glimpsed by referring to the Table of Contents, sensitive issues will not be avoided. Industrial terrorism, an outgrowth of espionage and a very real phenomenon, will be discussed, as will the finer points of military/industrial operations and the role of government in relation to industrial spying. Current source material derived from periodicals and recently published government reports will supplement many well known sources of information concerning corporate intelligence, such as Larry Kahaner's volume (1996) and a recently published book in the long respected Wiley series entitled Competitor Intelligence by Hussey and Jenster (1999). Some works listed in the Reference section of this report have been merely consulted for background material, whereas others have been formally cited.
Thinking in this field is neither static, nor stale. Industrial espionage, whether merely gathering competitive data or indulging in the most criminal of acts, is a constantly developing field of risk, action, counter-action and strategic study. There is also an ethical angle to review within the context of industrial espionage, particularly as technology changes so rapidly that what may have been acceptable today seldom is tomorrow, or, conversely, what was unacceptable yesterday may well prove, to be perfectly permissible in these contemporary times. Protection of the innocent, or the inventive, is not always possible, however, in this world of shifting loyalties and underhanded deals.
Thus, a panoply of considerations will be explored in this report, inclusive of case histories, observations and comments, shedding light on the shadowy realm of industrial espionage wherein massive sums of money, huge gains and devastating losses take place routinely. The fate of entire societies can hang in the balance, and the specific dynamics, tactics and strategies of surreptitious players, operating overtly or covertly, are essential to understand and appreciate, realistically, for what they actually represent.
This report, therefore, will provide insight into the multiplicity of methods, devices and ploys used by industrial spies at the end of the 20th century, and will explore the wider implications of industrial espionage in relation to the future of American economic primacy.
Lastly, the report will make several tentative recommendations for rectifying or neutralizing trends and practices that may already be too late to reverse, and will draw certain tentative conclusions.
II. Competitive Intelligence, Counter-Intelligence and Corporate Security
Review of literature in the field of industrial intelligence and counter-intelligence reveals that there is a growing sense of urgency as espionage and unlawful theft of data and technology continues to proliferate. Whether a given act is lawful or not is infrequently the critical factor. The type and nature of information stolen for use by competitors is far more crucial than whether the actual methodology by which it was obtained was legal. Companies must protect against all types of illicit transfer of data or technology whenever possible and by all means. Existing literature points to several pragmatic protective approaches which can be adopted by companies fearful of externally intrusive behavior, or behavior originating from within their own walls. The need to understand that company information is constantly at risk is of paramount importance. Indeed, economic and industrial espionage is becoming such a serious threat internationally and U.S. companies are rapidly becoming such familiar targets that urgent measures have to be taken, articles in World Business Today point out (CNN-FN, March 9, 1999). Indeed, executives of major companies are seeing their firm's innovative research being stolen and used by other firms, often without adaptation or even a feeble attempt to disguise the theft, for a small fraction of the cost it took their firm to develop the stolen process or technology. Due to gaps in existing patent regulations or fine points in fair trade or general business legislation, these ultra-costly thefts, sometimes lightly referred to as simple borrowings, are going unpunished. Costs of litigation, in the event someone is detected, are also a factor, of course. The most logical solution is to protect against the theft or surreptitious transfer in the first place. And, in fact, the need to protect larger sectors of proprietary data is becoming even more evident in specific industries.
Beyond mere protection, active measures within a company, in the form of counter-intelligence initiatives, must be taken to locate the source of leakage or infiltration. The number of industrial espionage cases has grown so alarmingly that both the CIA and the FBI have "beefed up" their economic intelligence programs and have assumed a prominent role in attacking this ever-spiraling dilemma. The targeted entities are either individuals or other firms from some 20 countries many of which are allies and friends in times of political instability. What is so disturbing is that, not infrequently, companies are being forced to take expensive counter-measures against entire governments. The playing field is rocky and strewn with pitfalls. Weak spots in firms, such as janitorial positions, are even being screened carefully in light of theft -- master-minded from above -- during the night shift or at odd times, such as week-ends or three-day holidays. Computer chips, diodes, capacitors, high-tech components have all been stolen during these shifts by low-level employees, bribed by foreign competitors who have tens of millions of dollars to gain and little, in an international climate of anonymity, to lose.
According to the CRIIR newsletter (July 1997), there have been extensive investigations by private security firms of industrial espionage cases, invariably involving US firms to some degree, in such countries as Argentina, Hungary, Russia and in the Caribbean islands of Turks and Caicos.
Many of these investigations involved outright criminal activity and even tourists were scrutinized in many questionable situations where they may have been in a position to acquire unauthorized information from American branch or subsidiary firms in Budapest, Buenos Aires or Moscow.
There is the entire issue as to whether, and to what extent, the U.S. government should involve itself in the protection of private American firms from fairly powerful outside forces. Indeed, if foreign governments are assailing American companies, then obviously the U.S. government should be notified and might well be entitled to play an active part in countering the invasive foreign entity.
The argument in favor of U.S. government intervention under such circumstances is that the primary justification of such involvement is the destabilizing impact that a foreign intelligence service, replete with resources, creates in terms of the otherwise normal competition between businesses. There is growing awareness of the sheer force of even, broadly defined, "friendly" entities such as the European Economic Community which is now surpassing the United States in gross productivity and excels in a number of high tech fields. Their fairly aggressive posture with respect to invasive activity is drawing the attention of important officials in Washington, New York and Los Angeles.
The value of a U.S. company that adds jobs, and infuses its profits into the economy is undeniably deserving of protection, those in favor of government intervention argue. When it comes to foreign-based espionage in the economic sphere, all firms should be allowed to act, in conjunction with their governments, to protect their vital interests. There seem to be few moral qualms about acting in a clearly unethical manner, even among otherwise allied nations. Pierre Marion, formerly the head of the French Intelligence Service, asserted on a number of occasions that the United States and France are "really allied" but that when it came to economic and technological competition, these two historical friends were very much at odds.
The financial motives are so tremendous in the illicit business of corporate stealth that it is actually a very cost-effective means of gaining an edge over the competition or even of smothering the competitor entirely. A few well-directed initiatives could allow poorer nations to achieve the same effect as if they had themselves invented a technological device which could infuse massive capital into their feeble economy. It's quite literally a matter of survival for some societies, such as the "new" Russia, undergoing these cash-starved circumstances.
The massive leakage of atomic secrets from Los Alamos National Lab probably at the hands of Mainland Chinese agents planted in or around the actual premises is a dramatic example of the need to establish viable procedures to protect secrets, whether military as in this case, or civilian, from theft and export to potentially hostile nations (CNN-FN, Mar 9, 1999) Counter-intelligence operations serve this purpose and are becoming more common, more indispensable and more critical to proper functioning of the modern American economy, in an attempt to minimize loss and maximize security. There are both economic and national security issues at stake in the theft of such secrets as those at Los Alamos, yet the same dramatic dynamics exist within firms such as Lockheed, Boeing or General Dynamics, all of which are involved with strategic products or services. Protection is clearly needed for laser systems, electronic armaments, navigational systems, computer technology and energy-related devices, to itemize but a few of the critical areas identified by government publications.
Fortunately the United States is well aware of efforts by foreign governments and firms with respect to the illicit acquisition of intelligence and has established many agencies, such as the National Counterintelligence Center (NACIC), to deal with this growing phenomenon.
III. Strategic Risks: Political Terrorism, Surreptitious Acquisition, and Computer Invasion
There is a very real threat in modern times of political terrorism affecting American industry in conjunction with a single act of espionage, or an entire sequence or series of such acts. When sensitive military technology is being developed and new developments considered vital to the defense of a nation are involved, then major firms, such as Northop Grumman or Raytheon, must begin to take anti-terrorist precautions in addition to initiating measures designed to prevent the outflow of critical data and know-how. Careful screening of individuals admitted to company facilities is indispensable, on a 24-hour basis. Electronic surveillance devices on the perimeter of company grounds are also being installed, and indeed, General Telephone and Electronics, at its Sylvania Sub-Division (Electronic Defense Laboratories) in Mountain View, California, has been using such devices for at least 40 years to physically deter intruders. This protective mentality sprang up during the Cold War and, currently, is being employed to guard against certain Asian and Middle Eastern countries which may be motivated to physically attack facilities. However, more astute plotters actually mastermind terrorist attacks from within the industrial setting itself. This was the case with the Beider-Meinhoff gangs in Germany and more recently in the United States, with respect notably to the World Trade Center bombing and less widely publicized hostile incursions at armament trade shows and product-marketing conventions.
If guarding against actual terrorist threat is important, through use of the latest technology to do so, other threats -- considerably more subtle -- must be countered by strategists and planners, as well. From within the confines of the plant itself, there must be a surveillance system and a means to deal with the distribution of memoranda, reports and technical documents. Most firms employ a multi-tiered security clearance system according to the conditions of which certain individuals are cleared for Top Secret documents, others for Secret and still others for Confidential. This 'classified document' system was pioneered during World War II, and later perfected, for use by the military but has also become standard in many defense-related industrial settings. It can be applied to the civilian commercial sector with minimal adaptation and, if properly designed, can restrict key documents and data to only those persons who have a need to know or who have proven themselves to be completely trustworthy. Internal documents if controlled tightly can be kept secret and will be used, therefore, only by authorized personnel whose motives are above reproach. In spite of precautions taken, classified documents or those "not-for-distribution" to the public are often the target of industrial espionage operations.
It is important to note that foreign governments and overseas industrial interests also collect what they may consider, on the surface, 'economic information', but it is frequently inclusive of vital technical data, from US firms through standard business practices, such as mergers and acquisitions, business alliances, licensing agreements, and other 'vehicles' for open-news dissemination. Although these activities are a universally accepted part of the business world, a large body of reporting indicates that competitors gain most of their information this way. The mere 'means' of gathering data do not necessarily imply that the data will be used in a friendly and legitimate fashion. Much of it can be put to use against US business interests, with rather somber implications for other segments of the economy and defense establishment. The protection of computer-stored data is equally critical to the interests of American industry. With incalculably vast amounts of data placed in vulnerable archives and depositories, it would seem a virtually impossible task to protect key files for all sectors of the American economy. Indeed, this responsibility resides with the individual companies who generate and store them. The Internet, of course, represents a great hazard to confidential information, especially when it is transmitted freely and openly. The former Soviet Union, and now reports indicate the "new" Russia, engaged, and continue to engage, in interception of microwave transmissions virtually everywhere they have embassies, trade delegations or other legitimate cover operations. In London, England, for example, due to the location of the Russian Embassy in relation to a huge microwave relay tower, some 80% of all private transmissions were routinely intercepted for years, providing the clandestine Russian listeners with vital information concerning the price of precious metals, stocks and bonds. This privileged information, among mountains of other strategic data, still enables the Russian hierarchy to reap massive profits and learn -- well in advance of other Western nations -- about decisions which could shape and reshape, obviously to the advantage of Russia, their foreign policy, adversely impacting the economies and defense postures of dozens of Western nations.
There is little doubt that, given what is known about the incursions already recorded and the obvious intentions of foreign nations, U.S. national security interests are clearly at stake unless strong counter-measures are designed, and implemented, to deter those who would dare to pose serious strategic risks to U.S. industry.
It is becoming increasingly apparent that information collection efforts on the part of invasive competitors will not be limited to the polite policies of standard business intelligence. The private sector must turn, therefore, in the absence of effective government involvement, to independent intelligence firms willing to assist them.
As the general standard of living in foreign nations increases and as these societies become more urbanized, industrial security and safety concerns take on an increasingly higher profile. Both the public and private sectors in Thailand, for example, as well as in other Asian and African nations, have seen large increases in security and safety purchases aimed at arming themselves against crime, general security problems and corporate intelligence initiatives. This growing concern involves, among other primary sectors, military, police, civil, industrial and commercial applications.
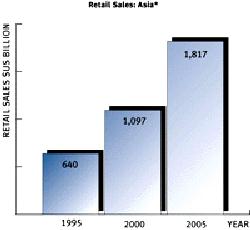
In support of this notion, Figure I, below , illustrates the rapid growth in Retail Sales of many Asian nations, and inferentially demonstrates that, as wealth increases, in this case threefold in a ten-year period, so do fears of increased intrusion, data collection, and industrial espionage. Indeed, several studies have referred to the correlation between economic growth and a resurgence of industrial intelligence activity, often in vital sectors. With such exponential growth in these key sectors, measures have to be taken to curtail intelligence operations here and abroad.

FIGURE I
(Source: KMPG Newsletter, 11/97)
These Asian figures indicate, by implication, that fears are growing there in proportion to the growth of business , but also expose the sad reality that, as their industries grow, so, too, does their incentive to cut costs and increase profits, often at the expense of the United States whose technology they have stolen. Examination of the clandestine collection methods used by Asian, and other, nations will prove to be an enlightening exercise.
IV. A Brief Review of Collection Methodologies Employed
Those collecting data infrequently use a single method. Most often there is a combination of techniques utilized to gather intelligence on competitors' processes or products. While their being mentioned here cannot imply that these are necessarily illegal activities, they are listed as potential elements of a much broader, often even a well planned intelligence effort.
Traditional espionage methods historically and typically are reserved for collecting national defense information. They are, however, more currently being applied to collect economic and valuable trade-mark or "proprietary" information. Traditional awareness training for those in targeted industries is most suitable for combating the effectiveness of these techniques.
Furthermore, an intelligence collector's most reliable source is a trusted person inside a company or organization to whom the collector can assign the "duty" of providing proprietary or classified information. Interestingly, a foreign collector's interest in a given company's employees is not necessarily commensurate with their rank or even their function within the company. For example, key researchers, mid-level business managers, and departmental executives can all be targets. Yet, so can support employees such as secretaries, computer operators, technicians, and even janitorial people serve the purposes of an intrusive campaign. The latter frequently have good, if not the best, access to competitive information, sometimes on the night shift and/or simply by intra-company theft. In addition, their lower pay and rank may provide fertile ground for manipulation by an intelligence agency, since foreign agents virtually invariably employ money as a classic lure.
It has been demonstrated that the individuals most likely to improperly acquire a company's information are the company's own employees. Employees who resort to stealing information exhibit the same motivations and human frailties as the average thief or spy. Frequently, their extra-professional interests or problems include illegal or excessive use of drugs or alcohol, money problems, personal stress, sexual gratification, or just plain greed. Obviously, foreign industrial agents (as opposed to political spies who sometimes use the same techniques) are ready to provide these commodities in exchange for proprietary information which could yield millions of dollars in profit for their firms and nations.
The Nixon era certainly taught America about surreptitious entry. Similarly, economic and industrial espionage may involve simply breaking into an office containing the sought data or information. Companies have even reported break-ins in which conventional lap-top computers or disks were stolen, even when there were easily obtainable, more valuable items in the same vicinity. These instances are not always reported, or are reported as merely break-ins, without considering the possibility that the target was "information" rather than equipment. It is both curious and disturbing that conventionally trained investigative personnel are still considering something as potentially valuable as a stolen floppy disk as if it were worth the 79 cents it costs to purchase it, ...empty.
Taking surreptitious entry even a step farther, some competitive firms or governmental agents, seeking industrial information, convince hotel operators to provide intelligence collectors with access to visitors' luggage or rooms. During these surreptitious break-ins, known informally as "baggage opportunities," unattended luggage is searched for sensitive or desired information, and any useful documents are copied or simply stolen. This is a particularly effective technique when the visitors are "in town" for a specific convention or trade show and are apt to have precise data, pricing information or product descriptions on hand to show serious clients or properly authorized persons.
Another widely used intelligence collecting technique involves technical invasion. This method includes computer intrusions, telecommunications targeting and a variety of intercepting activity which is becoming more and more common as security on the Internet becomes more highly vulnerable to penetration. There are also major gaps developing in the area of what may be called "private-sector encryption weaknesses". Computer invasion activities account for the largest portion of economic and industrial information lost by U.S. corporations, according to John F. Quinn, Director of Quinn & Associates (Viking 1994).
Because they are so easily intercepted, corporate telecommunications, especially international telecommunications, offer a highly vulnerable and lucrative source for anyone interested in obtaining trade secrets and confidential or competitive information. Additionally, due to the increased usage of these links for computer data transmission, in bulk format, and electronic mail, intelligence collectors find telecommunications intercepts extremely cost-effective. For example, foreign intelligence collectors routinely intercept facsimile transmissions through government-owned telephone companies, and the stakes are large. Approximately half of all overseas telecommunications facsimile transmissions are intercepted for industrial espionage purposes. Innovative "hackers'' connected to computers containing competitive information evade the controls and easily access companies' information. In addition, many American companies have begun using electronic data interchange, a system of transferring corporate bidding, invoice, and pricing data electronically overseas. Because this system is poorly protected, many foreign government and corporate intelligence collectors find the transmitted information easy to get and exceptionally valuable.
As is the case in political espionage, disinformation is sometimes injected into the industrial and economic circuit to confuse or perturb the normal flow of business data or intelligence. Amazingly, some governments also use disinformation campaigns to frighten their domestic companies and potential clients away from dealing with U.S. companies. It can be readily seen that this can cause damage to the U.S. economy, either directly and indirectly. Common breakfast conversation in Europe often deals with the inefficiency of American industry and many executives, who might be eager to deal with American firms are dissuaded by simple glances, handshakes and anecdotes recounted in informal contacts with fellow Europeans, often agents or plants.
Along this same line of thinking, press and government agencies frequently discuss foreign economic and industrial intelligence activities, purposely in vague, non-specific terms. The press has been used to describe foreign competitors or countries as aggressive and untrustworthy, even if the accuser has no tangible evidence of any collection activity. Further, it is becoming increasingly known that some countries have widely publicized their efforts to set up information security mechanisms to protect against their competitors' penetration attempts, and frequently the United States is mentioned as the primary threat. So the sword cuts both ways. Not only is intelligence conducted against the U.S., but campaigns aimed at discrediting the quality or motives of U.S. industry are also launched. Together, these strategies can be devastating.
Little spoken of on our nation's campuses is an increasingly popular and notoriously effective approach. Foreign students studying in the United States are asked to gather intelligence and are actually quite efficient at doing so. Their motives, sometimes transparent, may be nationalistic, monetary, sexual or career-oriented. Many foreign governments 'require' foreign students specifically to acquire information on a variety of economic and technical subjects, as part of on-going financial support for their studies. And, in some instances, countries select students before they come to the United States to study and subsequently request that they send any technological information they acquire, either routinely or under special orders, back to their home country. Others are approached after arriving and are recruited or pressured based upon a sense of loyalty or fear of their home country's government or intelligence service. They may even be approached by third-country governments, and ensnared in a morass of monetary, sexual or academic blackmail schemes.
In some astonishing (but very real) instances, at an intelligence collector's request, foreign graduate students serve as "assistants" at no cost to professors doing research in a targeted field. Technical universities are most often the sites of these types of collection strategies. Obviously, the student has access to the professor's research and learns more and more about the technical applications of the professor's innovations or discoveries. The Physics Department, as an obvious case in point, at New Mexico State University, is honey-combed with Asian students who have easy 24-hour access to high capacity data transmission technology, such as FTP programs, all of which are unencumbered and interconnected with their homelands at the speed of light. Recent discoveries at the university can be applied by Asian industries in a matter of weeks.
As is being uncovered in the Los Alamos case, foreign companies and governments sometimes recruit employees of their own nationality within a U.S. firm to steal proprietary information. Although this is similar to clandestine recruitment used traditionally by intelligence services, often no actual intelligence service is involved, only a competing company or non-intelligence government agency, although, admittedly, its agents sometimes act in conjunction with a national intelligence agency. The planted collector, freely but cautiously, then passes critical information directly to a foreign firm or to his or her government for use in its research and development activities.
Without naming them, a number of foreign countries actively debrief their citizens after foreign travel, asking for any information they may have located during their trips abroad. Sometimes these debriefing sessions are vigorous and exhaustive, with some foreign scientists describing them as plainly offensive. In other countries, they are simply an accepted part of traveling abroad, and tourists realize this fact of life prior to departure. U.S. counter-espionage services sometimes provide false information to tourists suspected of being just a bit too curious and this technique has proven to work well in deceiving foreign governments as to U.S. capabilities or development plans
Industrial intelligence collectors find it rewarding to target persons of their own ethnic group. They particularly seek individuals working in the U.S. military and R&D facilities. The targeted individuals must have some level of access to proprietary and classified US technology. Several countries have found that compelling these 'targeted' foreign ethnic scientists to return to their homelands is the most beneficial illicit "technology-transfer" methodology. One country, according to Asian sources, quoted in The South China Morning Post (SCMP Archives, 1999), claims to have repatriated thousands of ethnic scientists back to their home country from the United States. It is a sad fact of intelligence gathering activities that ethnic targeting includes covert attempts to recruit naturalized U.S. citizens and permanent resident aliens to assist in acquiring U.S. technical data and information. Frequently, foreign intelligence collectors appeal to a person's original patriotism and ethnic loyalty. Some countries' collectors resort to threatening family members who continue to reside in their home country. This is a particularly effective tactic and, unfortunately, has resulted in the transfer of valuable information.
There are, of course, dozens of other methods of collecting data which could be discussed, although many of them build on the concepts included above. Coercion, force, money and need-gratification are all part of this profitable game, which takes shameless advantage of human behavioral weaknesses and patterns most of which are well known to counter-intelligence agencies, private and governmental, in the U.S.
Naturally, since federal governmental agencies in this country are clearly reluctant to act within the area of industry, the private 'security' sector is beginning to blossom. Dozens of new security or intelligence-oriented firms are coming to the assistance of American firms undergoing problems of intrusion, collection or infiltration.
V. Advanced Military Technology and Industrial Espionage
The Defense Advanced Research Projects Agency (DARPA) supports the U.S. Department of Defense (DOD) in all advanced military research and development initiatives. Because the interfacing of private industrial capability with the military is an integral part of America's defense efforts, any seepage of information regarding even seemingly innocuous technology such as tool and die making, for example, could be considered a major breach of national security. Although this is definitely the case, such technology (from small components up to the actual armament being fabricated) is readily available (1) on the Internet, (2) in defense magazines, (3) from armament conference reports, and (4) in easily obtained industrial briefs, memoranda and technical manuals. If all of these "open" sources are consulted in unison, a reasonably complete profile of the military technology, and its vital components and sub-systems, desired by the intelligence agent can be obtained. DARPA's Technology transition report (1997) is a valuable source of detailed knowledge, often quite precisely presented, concerning the latest defense and weaponry technologies under development in the United States.
If anyone wanted to know, for example, about such items as the MK 50 Torpedo Propulsion System (SCEPS) or the "MIRACL" Anti-Ballistic Missile Defense System, careful study of this document would suffice. Sometimes charts and graphs are provided with vital data generated from tests or trials. High energy laser technology, according to DARPA publications, is still another area where intelligence gathering takes place within the U.S. industrial-military context. Developments in this field are critical to U.S. Defense Systems and stolen or pilfered technology, especially from within academic departments at the Graduate Level, is doing serious damage to American interests, cutting 'lead time' over potential enemies to the mere minimum. Recognizing this threat, and in order (1) to protect effectively against the development of military and strategic weapons, most of which are manufactured by private industry in the United States, and (2) to be constantly aware of new technology emerging from other nations, the Defense Department authorized creation, in 1958, of the agency introduced earlier in this report-segment, DARPA.
The agency was established in 1958 as the initial U.S. reaction to the Soviet launching of Sputnik. Since that period, DARPA's principal mission has been to assure that the U.S. maintains a lead in applying state-of-the-art technology for military use and to prevent technological surprise from her adversaries. Part of DARPA's duties include seminars offered to industrial managers keeping them updated on the latest risks in espionage and intelligence-collection strategies in use by foreign or unfriendly entities. The DARPA organization was originally as unusual as its role, reporting directly to the Secretary of Defense and operating in coordination with the military R & D establishment, much of which is privately funded and, in fact, commercial. Strong support from the upper-echelon Department of Defense management has always been essential since DARPA was designed to be a 'contrastive force' in relation to the pre-existing, conventional military R&D structure and, in fact, to be a deliberate counter-point to traditional organizational models and paradigms.
The guiding philosophy of DARPA has, from the outset, been to guard against advances by other nations and to protect American defense secrets, often by reaching into the private industrial sector to do so. Unfortunately, it is not an agency with massive enough funding or capabilities to effectively fight and combat the vast amount of industrial espionage which takes place within American industry and on U.S. campuses.
Some of the more important features of this highly protective agency, skilled in both counter-intelligence tactics (often through interface activities with other agencies) and in ensuring development of state-of-the-art military technology for U.S. use, are itemized in Figure II, below.
1. Relative compactness and flexibility are considered advantageous characteristics. 2. Significant autonomy from other bureaucratic organizations is maintained. 3. Technical staff is drawn from top-notch American and screened world scientists. 4. All R&D efforts and intelligence-gathering initiatives (if necessary) last 3-5 years.
(Source: Adapted from DARPA Mission Statement at http://www.darpa.mil/mission.html )
FIGURE II
Whatever organizational changes may be made in the near future within DARPA and similar U.S. defense-related agencies, will be designed to protect sensitive data from intruders and to guarantee, indeed ensure, that the most recent technology from the private sector is put to use within the U.S. defense industry, as new armaments and weapons systems emerge.
VI. Extent and Nature of Government Protection of Private Sector Firms
The potential threats posed by the activities of foreign firms or agencies engaged in what could be construed as offensive economic industrial or military espionage cause most observers to agree that intelligence services do, in fact, have a legitimate role in defending against such intrusions. Even a defensive role for intelligence services, however, raises several troublesome issues.
If intelligence services are to play an increased role in defending private sector entities against economic espionage, they will require a clear-cut ' mission statement' as to what they are defending against. The key question is whether a foreign government must be involved either in conducting or facilitating the economic espionage before the domestic intelligence service, in this case the new mechanisms being set up in the U.S. to cope with economic espionage, would be justified in acting.
Note: It is necessary to keep in mind that the United States, well before the days of
former CIA Director James Woolsey, unlike most nations, has 'ruled out', under all
scenarios, the involvement of the CIA in private industrial espionage matters. (Gertz, 1993)
However, if intelligence agencies were permitted to involve themselves, as they do in France and Canada, their assignments would be fairly 'comfortable' from the point of view of intelligence services since they typically conceptualize and direct their activities in terms of nation states. In the world of industrial espionage 'reality', as we have established, nation states do in fact operate covertly in this theater of undercover, outright theft and unauthorized technology transfer.
Those who favor requiring foreign government involvement as a necessary condition for intelligence service action, whether in the U.S. or elsewhere, argue that the primary justification for involvement is the destabilizing effect a foreign intelligence service, with all its resources, brings to bear on the competition among businesses. In this view, the damage foreign government economic espionage does to the 'playing field' merits bringing in the domestic intelligence service to even the odds.
Competitive industrial espionage between companies, foreign involvement or not, is simply part of the rough nature of the business world, and intelligence services should not get involved. This, however, may be easier said than done. While simple in theory, the strict requirement of foreign government involvement becomes rather complex in practice. In many cases it is difficult to determine if the principals involved in an economic espionage operation are being directed or facilitated by a foreign government. Another problem with a strict focus on foreign government involvement is that such a (narrow) focus ignores the important issue of the potential impact of the specific economic espionage operation involved. It can be argued that the activities of large multinational corporations, with their wealth of intelligence resources, may be more of a threat to a country's economic security than 'amateurish' attempts by tiny, under-resourced entities that happen to be full-fledged nations.
The growing influence and global reach of some of these organizations puts them on a par with all but the most powerful nations. As a case in point consider the relative power of this single corporation (Figure III below) in relation to that of entire nations:
Pfizer Corporation and the group of multinationals it organized to have intellectual
property issues addressed in the GATT had more influence on the intellectual property
provisions of the Dunkel Draft of the Uruguay Round than all but a handful of states.
(Source: GATT Proceedings, cited in CSIS, 32)
FIGURE III
The case for the prerequisite of foreign government involvement is further weakened by the fact that intelligence services ALREADY involve themselves in certain matters regardless of the presence of government.
As we were implying earlier in this report, terrorists are neither (officially) directed nor supported by foreign governments, yet governments feel no qualms about involving their intelligence services in this area: the impact of terrorist activities is deemed sufficient to warrant attention by most domestic intelligence services. In the case of the U.S., the FBI tends to investigate.
Governments struggling with this issue will have to determine whether potential economic losses and their implications are to be given equal weight in relation to the physical security of their citizens.
VII. National Alliances and Industrial Espionage: A True Dilemma
Traditionally, intelligence services operated in a world of nation states neatly divided into camps of allies and adversaries. In the diplomatically difficult realm of economic espionage, however, this comfortable distinction no longer applies.
On the turf of economic espionage potential adversaries could well be one's own military and political allies. To the extent that a country's economic interests diverge from its military or political interests, economic espionage forces intelligence services, like modern corporations, seem destined to compete and co-operate at the same time. This potential conflict between a nation state's commercial interests and the military or political interests it shares with its allies explains some of resistance intelligence services have demonstrated when faced with this delicate issue.
Re-thinking and realigning potential adversaries, especially those who were once friendly, also has the potential to undermine traditional intelligence-sharing networks in many sectors. In a world where business must no longer be secondary to the now-resolved Cold War, and where unfair trade practices are seen by some specialists as the economic equivalent of an act of war, commercially valuable intelligence may be shared much less freely within military and political alliances. It is interesting to speculate whether the traditional intelligence-sharing networks that deal in military and political matters will soon find their equivalents in economic intelligence-sharing networks. In my estimation, this is likely to occur, in order to enhance the benefits of mutual protection against common commercial adversaries. Already, in France, that nation's two largest retail chains are merging in an unprecedented effort to ward off the impending arrival of Walmart, now the world's most formidable retailer (Le Monde, August 21, 1999). Behind the scenes competitive intelligence operations in this instance must have been dramatic and intense.
At the outset, these networks would most likely encompass regional economic agreements, such as the EEC and NAFTA. In the near future, it is conceivable that the U.K. would share more economic intelligence with fellow EEC members than it would with Canada or the United States.
On the other hand, the U.S. would be more likely to share its economic intelligence with its fellow NAFTA members. Given that the EEC is the most mature and comprehensive of these regional agreements, it is likely pressures for any changes of this nature would first arise within the actual EEC structure. Certainly in the area of international trade negotiations, this intelligence- sharing split between North America and the EEC is already present. As time passes, however, even economic intelligence-sharing networks based on regional trade groupings may seem too rigid. Nation states, and perhaps even some well-defined economic zones within these states, may turn to what specialists refer to as more "time-limited, goal-oriented" tactical alliances necessitating more flexible economic intelligence alliances.
In either case, new and strengthened alliances based primarily on economic interests will certainly test the durability of older military and political alliances. It seems inconceivable that a military or political alliance would not be weakened if the countries involved were members of separate competing economic intelligence-sharing networks representing rival trade groupings. In other words, economic tensions may, as history has demonstrated, ultimately lead to military rivalries.
With reference to this specific dynamic, the emergence of China as one of the major engines of economic growth for both Asia and the world and the ultimate nature of its relationship with Japan bears watching.
Almost every analysis of economic espionage raises the issue that intelligence service involvement may be a waste of resources, given the "stateless" nature of multinational enterprises (MNEs). Supporters of this view see no logic in a nation state assisting MNEs, as they have no commitment to any particular country and will simply use any defense they are provided or any information they receive to optimize the productivity of their global network. The result is that any benefits the nation state derives by providing intelligence or protection to MNEs will be purely casual and informal. These observations, however, miss the point that enterprises striving after profit were NEVER expected to put the interests of their investment jurisdiction over their own.
In the view of supporters of a defensive role for intelligence services in economic espionage, as was asserted earlier in this paper, a company that provides employment and adds value to the domestic economy is an asset worth protecting, regardless of its stateless character. Further, in protecting these companies it could be argued that the nation is also protecting its investment climate which could be damaged if it became known that the country was relatively lax in its watchfulness against economic espionage, and therefore posed a greater risk for investors.
VIII. Overview, Assessment and Recommendations
With more than $250 billion dollars in high level technology stolen in the United States annually that (1) seems to be surfacing in available figures, and (2) countless hundreds of billions in unknown and unrecorded losses occurring in the same time frame, it would seem as if this nation, and perhaps the U.K. and France as well (all allies, and yet trade enemies when it comes to money and state-of-the-art development) are experiencing a major crisis.
Little seems to be "verifiably known" about the true scope of industrial espionage in either this country or in Europe. The figures that have been provided in this report point to alarming trends, many of which have gone unchallenged in the last two decades. Several partially effective counter-intelligence initiatives are in operation, but many are being delayed due to hesitation on the part of the government to 'become unduly involved' in the private sector. The inherent qualities of 'capitalist independence and sacredness of the private sector' are actually leading, ironically, to the seepage, pilferage and loss of information vital to the security of the country.
Indeed, it would seem as if the private sector itself is suffering inwardly from the theft and counter-theft of data and trade secrets. Massive forces, all motivated by capital gain or by ideological primacy, are tugging art the very heart of American industry which continues to excel in the innovation of new concepts, but which cannot protect its key data from external attack. This is not to say, simplistically, that American industry is an innocent and naive victim of foreign entities; on the contrary, the game is also played within the boundaries of this country and it is aggressively played by American multinational or global firms abroad as well. Over martinis and shrimp, conversations often verge on disclosure even within the first five minutes of acquaintanceship -- out of professional vanity, pride or motivated and misplaced loyalties.
Today, as we have discussed, the number of industrial espionage cases has increased so dramatically that both the FBI, domestically, and CIA, to a limited and circumscribed degree when security issues are at stake, have enhanced their economic counter-intelligence programs and have taken a leading role in confronting this growing problem. The FBI is currently investigating allegations of economic espionage activities against the U.S. by individuals and/or organizations from more than two dozen different countries, according to independent observers. U.S. businesses are also being forced to deter and repulse the professional spy services of foreign countries, even those that can be considered traditional allies. As summarized earlier, most informed and cautious firms are now taking charge by implementing stringent security measures, including classifying documents and screening all applicants, at all levels.
When traveling abroad, business executives are increasingly vulnerable to the devices of a foreign intelligence service or even of private corporate intelligence-gatherers. Therefore, representatives of companies must take the necessary precautions to protect their corporate secrets, not only for the economic viability of their businesses, but also for the economic safety and well-being of their nation. Travelers to foreign countries should consciously expect intelligence services to conduct such activities as surveillance and electronic eavesdropping via telephones, fax machines and placing electronic "bugs" on selected seats on national airlines (Air France is a famous case, according to Canadian intelligence services) in an attempt to obtain wanted information. Such intrusions can be very extensive and even casual conversations are being monitored now for subtle hints or even tangential reference to business deals, price-structures, impending mergers or technological advances, either in general terms or in more specific contexts.
Mention has been made at some length of the risks inherent in the military sphere. Eighty to ninety percent of often critical and strategically useful information is available through open publications such as the DARPA documents cited earlier in this report. While it can be argued that potential enemies are given just enough information to convince them of American supremacy in weaponry, the mere fact that concepts are discussed in considerable detail is, at the outset of R & D in a foreign nation, extremely helpful.
Beyond openly published material, of course, there are maintenance and repair manuals readily available practically for the asking in aircraft hangars and non-securitized technical offices. Putting all of this material together gives foreign governments or industrial competitors virtually all but the final elements of whatever "equation" they are seeking. The most famous example of this, not requiring formal citing since it is so widely known, is the development by India of its atomic bomb. Due to the prolific knowledge-base of Indian physicists, they were able to produce all components of the atomic bomb in practically no time. However, years, indeed decades elapsed, until they could discover or intercept (perhaps through industrial and military intelligence operations based in the United States) the technology required for the detonating device, representing perhaps only 2% or less of the required components. The detonator technology was highly guarded (and still is) for decades by the Russians and the United States, and formed the final barrier for many now-nuclear nations. That the fate of nations hangs by such a thread is truly alarming. And, similarly, on a more retail-oriented scale, it can be hypothesized that Kelvinator had to worry about guarding its refrigerator door-lock mechanism from duplication by Frigidaire engineers. The degree of success, whether atomic weaponry or refrigerators are at stake, in protecting one's technology relies on the many factors explained in this report, among which are: counter-intelligence, security systems, personnel checks, industrial policies and procedures, or government intervention, as warranted.
It is perhaps obvious that this report has not dwelled on the intricacies of ethics, intellectual property protection or some of the finer points of the various ideologies and socio-economic factors which may well lie behind most of the industrial espionage environment at the very end of the Twentieth Century. It has not laboriously discussed the Japanese or Chinese position on corporate intelligence, although much literature exists on this Asian perspective and resultant phenomenon. Rather, this paper has emphasized the tangible risks, the methods of intelligence operations, as well as the parameters of governmental responsibility, plus the latest in strategic counter-intelligence paradigms with peripheral reference to certain operational systems.
In this analysis, it has been established that real risks exist and that the fate of nations demonstrably hangs in the balance. The role of the industrial manager in this disturbing scenario has also been broached. Indeed, the manager must forestall any concerted attempt at theft or unauthorized transfer of data originating from "within" or from "without" his firm. He must also weigh the effects of his actions on his company, his society and his government. These dynamics are surely quite delicate and require insight, breadth of knowledge and a courageous sense of purpose and determination. As a responsible administrative and highly trained technical employee, the industrial engineer/ manager must also be aware of all the described nuances and subtleties of this dangerous and challenging field. The stakes are simply too high for America and for the Industrial Establishment of this country, and of Western Europe which embraces many of the values cherished in the United States, to ignore the on-going threats emanating from rogue regimes and unstable social systems worldwide.
We must never lose sight of the menace lurking within and on the perimeter of America's industrial infrastructure. Intelligence agencies throughout the world have re-energized their efforts and their commitment to pursue efforts in the area of economic warfare. We should not lose sight of the fact that American industry is their primary target, principally military, high-tech and computer related research. Smaller nations, such as Kuwait, already a proven ally and friend of the United States, depend on the integrity of American industry and on its continued efficiency, primacy and dominance in a dangerous and unstable world.
IX. References and Works Consulted
Bozeman, A.B., Strategic Intelligence and Statecraft: Selected Essays, Brassey's (US), Inc., Washington, D.C., 1992.
Canadian Security Intelligence Service, Commentary No. 32, May 1993.
Daboub, A.J., Top Management Team Characteristics and Corporate Crime, A Dissertation, University of Texas at Arlington, 1991.
Farr, R., The Electronic Criminals, McGraw-Hill Book Company, New York City, 1975.
Franklyn, D.J. "The Apparent Manufacturer Doctrine, Trademark Licensors and the Third Reinstatement of Torts", Case Western Reserve Law Review, 49:4 Summer 1999, 672-729.
Gertz, B. "CIA Chief Rejects Industrial Spying", The Washington Times, November 24, 1993, A3.
Hayes, R., Pisano, G. and Upton, D. Strategic Operations: Competing Through Capabilities, Harvard Business School, The Free Press, New York City, 1996.
Heims, P. Countering Industrial Espionage, 20th Century Security Education, Ltd, Surrey, England, 1982.
Hussey, D. and Jenster, P. Competitor Analysis: Turning Analysis into Success, John Wiley & Sons, Chichester, 1999.
Kahaner, L., Competitive Intelligence, Simon and Schuster, New York City, 1996.
Le Monde Selection Hebdomadaire, 21 August, 1999, http://www.lemonde.fr
McGonagle, J. and Cella, C., Protecting Your Company against Competitive Intelligence, Quorum Books, Westport, Conn., 1990.
McKendall, M.A. Within the Hallowed Halls: The Relationship between Corporate Structure, Corporate Culture and Corporate Crime, A Dissertation, Michigan State University, Department of Management, 1990.
Platt, W., Strategic Intelligence Production, Praeger Publishers, New York City, 1957.
Roukis, G., Conway, H., and Charnov, B. Global Corporate Intelligence: Opportunities,Technologies and Threats in the 1990s, Quorum Books, New York City, 1990.
Samuelson, P., "Intellectual Property and Contract Law for the Information Age: Forward", California Law Review, University of California, Berkeley, 87:1, January 1999, 1-16.
......................., South China Morning Post, Archives Data Base, 1999.
Stone, C., Where the Law Ends: The Social Control of Corporate Behavior, Harper and Row, New York City, 1975.
Tang, V and Bauer, R., Competitive Dominance: Beyond Strategic Advantage and Total Quality Management, Van Nostrand Reinhold, New York City, 1995.
Vaughan, D., Controlling Unlawful Organizational Behavior: Social Structure and Corporate Misconduct, University of Chicago Press, Chicago, 1983.
Volkman, E., Espionage: The Greatest Spy Operations of the 20th Century, John Wiley & Sons, New York City, 1995.
Wasson, B.D., "Copyright Implications of 'Unconventional Linking' on the World Wide Web: Framing, Deep Linking and Inlining", Case Western Reserve Law Review, 49:1, Fall 1998, 181-256.
Wilensky, H.L., Organizational Intelligence: Knowledge and Policy in Government and Industry, Basic Books, Inc., New York City, 1967.
Internet Sites Consulted
http://www.opsec.org/OPSOnline/NACIC96.html
http://www.ccnet.com/~suntzu75/jindesp.htm
http://cnnfn.com/worldbiz/9903/09/china_scope_pkg/#TOP
http://www.kslaw.com/menu/espionag.htm
http://users.erols.com/crintl/inv_news.htm#top)
http://taeng.com/industry/mag_ed/0295ics/ics0497.htm
http://asiabiz.com/cems/v1.html
http://www.aspac.kpmg.com/asiasphere/97nov/industry_outlook.html
http://www.darpa.mil/
* * * * * * *